All data is stored in a computer is expressed in a series of zeroes and ones (1 / 0) in the form of binary digits (bits). With magnetic particles, which can be polarized magnetic north or south, and that their magnetic poles may be changed or magnetic polarity of the voltage is sufficient to record, except that the order of the bits on the disc, which collects the particles needed for magnetic media for storing, in order to represent the stored data. Hard drives are defined, which contains two runways intersect and sectors. The goal is to provide a logical data structure to provide a means to distinguish between data fields. Within each theme, a number of sectors. It is in these sectors on the disk that stores data. The minutes of a hard disk is covered with a layer sensitive to magnetic fields is mainly composed of charged particles and magnetic recording as a whole can be called the recording medium. These particles can be adjusted to represent the magnetic bits, by inducing an electromagnetic field to them, a reader / writer. The recording medium contains billions of microscopic particles, given similar miniature metal shavings.
How does a database on your hard drive?
All data is stored in a computer is expressed in a series of zeroes and ones (1 / 0) in the form of binary digits (bits). With magnetic particles, which can be polarized magnetic north or south, and that their magnetic poles may be changed or magnetic polarity of the voltage is sufficient to record, except that the order of the bits on the disc, which collects the particles needed for magnetic media for storing, in order to represent the stored data. Hard drives are defined, which contains two runways intersect and sectors. The goal is to provide a logical data structure to provide a means to distinguish between data fields. Within each theme, a number of sectors. It is in these sectors on the disk that stores data. The minutes of a hard disk is covered with a layer sensitive to magnetic fields is mainly composed of charged particles and magnetic recording as a whole can be called the recording medium. These particles can be adjusted to represent the magnetic bits, by inducing an electromagnetic field to them, a reader / writer. The recording medium contains billions of microscopic particles, given similar miniature metal shavings.
Keep Laptop in Good Condition
1. Do not ever put a heavy burden on the laptop if we put the goods that have a heavy burden on the laptop, it can cause scratches on the LCD screen.
2. Avoid placing the laptop inside the bag with items that are too full of stuff .. because it will cause pressure on the laptop
3. note the temperature condition
Laptop or notebook is composed of various electronic components whose performance is affected by temperature. Among other things, the temperature is too extreme, such as too hot or too cold, can disturb the performance or even damage the laptop. Therefore, avoid the habit of leaving the laptop in the carwhich was parked under the hot sun. Avoid also highlight the laptop is under direct sunlight. Generally, manufacturers recommend a temperature between 5-35 degrees Celsius. Meanwhile, to the height recommended laptop to work at an altitude below 2,500 meters above sea level.
4. Storage
If you will keep your laptop in a long time (one week more), should remove the battery and store in a cool, dry, and circulate air well enough. Place the silicone gel to prevent mildew. So want to use it again, stun or content of the battery byfilling and emptying as many as three times in a row.
5. Avoid magnetic fields
To protect the existing data on the hard disk, do not place devices that contain magnetic fields / strong electromagnets around a laptop. From these devicesproducing magnetic fields, such as speakers are not shielded (unshielded speaker system) or cellular telephone. If you want to access the Internet using the facility infrared on the phone, put the phone in the distance about 15 cm from the laptop.
6. Use stabilizer
If you are working on a laptop with the use of electricity (without batteries), then you should use a stabilizer that can prevent the occurrence of an unstable electrical voltage to your laptop.
7. Deadly correctly
Never turn off the laptop while the hard drive indicator light is still blinking. This indicates the hard disk is still active. The loss of power suddenly (eg when the laptop is turned off) can cause data loss or interruption of performance on the hard disk. Make sure the hard drive light was switched off before you shutdown the laptop.
8. Avoid too soft surface
Do not place the laptop when the lights in place with a surface that is too soft as a sofa or mattress, so the laptop to be seen rather drown. This is very dangerous, because it can inhibit the release of heat from the laptop and make the laptop overheating.
9. Hinges monitor
If observed closely, in the folds between the CPU and the LCD monitor there is a hinge that allows the two components were clenched to each other. Be aware that the heaviest burden in a laptop is in partthese hinges. Therefore, do not give a snap when opening the monitor when going to activate the laptop. Vice versa, do not be too hard to close the monitor when finished using the portable computer.
10. Do not disassemble the laptop.
Dismantle their own laptops or not by experts, is a very unwise action. Laptops are not like ordinary radio or tape recorder. Many parts of the very small of the manufacturer have been assembled using robotic precision. If you're careless, then your laptop could be damaged severely. Always carry a defective laptop to the IT or the service center of your laptop.
That's 10 tips for caring for laptops are always in good condition
Step by Step Fix Regedit
Generally we click the program icon in the start menu or on the desktop to run certain programs. But the utility programs are not all available in the start menu or the desktop. These programs (such as Regedit.exe, cmd.exe) usually run through the Start menu> Run. What can we do if there is no Run menu in the start menu?
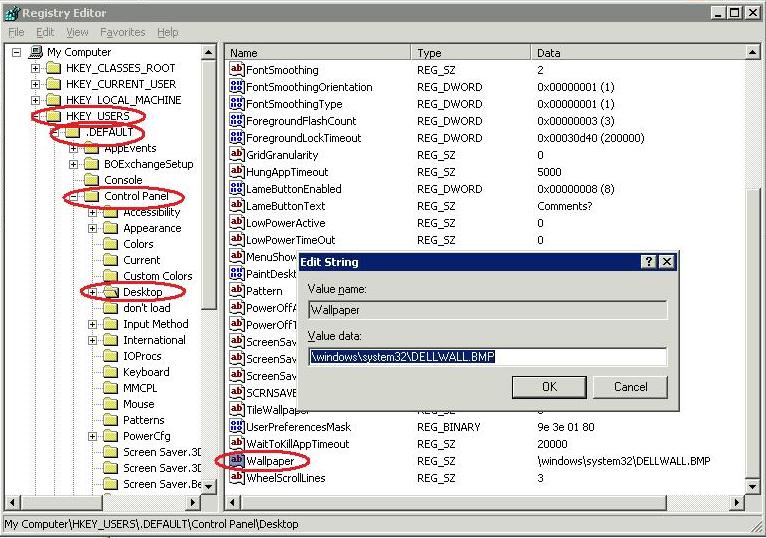
a. Utilizing Windows Explorer
Run the Windows Explorer, locate the file you want running the program in the folder C: \ Windows, or in C: \ Windows \ System, or in C: \ Windows \ System32. Then double-click on the file program.
b. Utilizing the Command Prompt (cmd.exe)
= Click Start> Programs> Accessories> Command Prompt, or run cmd.exe with the first way above.
= Type in the name of the program you want running, then press enter.
C: \ Documents and Settings \ mr. orche!> REGEDIT
c. Using Batch Files
= Run Notepad through the start menu or through Windows Explorer.= Type in the name of the program who want to run, for example, "regedit" (without quotation marks).= Save the file using the extension. Bat, for example, "TES.BAT".= Run the file. Bat it through Windows Explorer (double click).
d. Using Task Manager (taskmgr.exe) (Windows XP)
= Press Ctrl Alt Del.= Click button [New Task ...] on the Applications tab.= Type in the name of the program, and press enter.
e. Browser exploit Files in ACDSee
ACDSee = Run from the Start Menu.= Find the file you want running the program in the file browser window.= Double-click the program file.
2. Alternative ways of Registry Operations
If you can not run regedit, registry operations can still be done with some of the following alternatives:
Alternative 1: Using the command REG
1. Run Command Prompt (cmd.exe).
2. To see a list of key and value, use the REG QUERY command lokasikey.Example:REG QUERY HKLM \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ ExplorerREG DELETE HCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
3. Type REG DELETE namakey / V namavalue to remove certain value.
Example:REG DELETE HKLM \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer / V NoRunREG DELETE HKCU \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer / V NoFolderOptions
Note:
= Root name should be abbreviated, HKCR for HKEY_CLASSES_ROOT, HKLM for HKEY_LOCAL_MACHINE, HKEY_CURRENT_USER to HKCU, HKU to HKEY_USERS, and so on.
= For key names that contain spaces, key name enclosed in double quotation marks.
= To find out more about the operating procedures using the REG command, type "REG /?" Without the quotation marks.
Alternative 2: Using files. REG1. Run Notepad and type as the following example:
The new format (WinXP):Windows Registry Editor Version 5.00[HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer]"NoFolderOptions" = dword: 00000000
Old format (Win9X/NT):REGEDIT4[HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer]"NoFolderOptions" = dword: 00000000
2. Save the file with the extension. REG, then double click on. Reg file that you saved.
Explanation:
= First line, "Windows Registry Editor Version 5.00" or "REGEDIT4", is a fixed rule to mark the registry file.
= Second line, "[HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer]" indicates the location of the registry key, where the list value with the value data mentioned below will be stored.
= Third line, "NoFolderOptions" = dword: 00000000, value names and data they want to value them. In this example the mean change / give the data value 0 at the value named "NoFolderOptions".
= File is typed regedit winxp format (new format) or long format (Win9X/NT), both of which can be used for Windows XP, but the old format can only be used for Windows 9X/NT.
Alternative 3: Using a Startup Disk (only valid for Win9x)This method is the most difficult, and perhaps the only effective way to restore the registry when the system is already completely paralyzed.
1. Boot using the Startup Diska. Enter your Win95/98 Startup Disk into the floppy drive.b. Restart (make sure the configuration settings in the BIOS boot sequence pointing to the floppy).
2. Go to the directory (folder) C: \ WindowsA: \> C:C: \> CD WINDOWS
3. Do the export of data from the registry to a file. Reg specific for the desired keyFormat command:REGEDIT / E namakey namafilereg
Example:REGEDIT / E HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer TES.REG
If the key name contains spaces, use quotation marks:REGEDIT / E "HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer" TES.REG
3. Reach the Back Menu Folder Options in Windows Explorer
Some viruses need to hide certain files that the user (computer user) is not aware of the virus and% 0mengetikkan following command at C20agar removed the virus more difficult, by creating a hidden file. File hioleh user if the Folder Options settings on the option 'Show hidden files and folders' enabled. Sometimes even this menu be eliminated by the virus to ensure the virus files remain invisible. To hide the Folder Options menu, the easiest and most commonly applied by the virus is to change the registry settings, by inserting the value "NoFolderOptions" is worth 1. To bring back the Folder Options menu, this value should be removed, or changed the value to "0".
= To alter the Folder Options, click the Tools menu> Folder Options in Windows Explorer.
= Value NoFolderOptions the registry are either or both of the following locations:
HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
Value can be removed by using the REGEDIT program, or by typing the following command in Command Prompt:
REG DELETE HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer / V NoFolderOptions
REG DELETE HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer / V NoFolderOptions
4. Reach the Run menu
Delete value "NoRun" or change the value to 0 by using the registry operation (see sample registry operation to raise above the Folder Options menu). Value "NoRun" is in the key:
HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
5. Bring up the Find menu
Delete value "NoFind" or change the value to 0 by using the registry operation (see sample registry operation to raise above the Folder Options menu). Value "NoFind is" at the key:
HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
6. Enabling REGEDIT
Sometimes it can not be executed because REGEDIT be disabled via registry settings by the virus. To recover, delete the value "DisableRegistryTools" or change the value to 0 by using the Command Prompt (for WinXP), or by creating a file. REG (only for Win9x).
7. Reach the Hidden Files with Command Prompt Change the attributes Through
Hidden files (hidden) can be raised without playing the Folder Options, but by disabling the hidden attribute on the file. Hidden file attributes can only be changed in Windows Explorer if the Folder Options settings allow hidden files displayed. The alternative is to change the attributes of the file via Command Prompt. To list hidden files via Command Prompt, use the command "DIR / AH". Next use the attrib command followed by the parameter attribute to be changed. The following example can be used to disable the hidden attribute, read only, and the system at once, on all files in current directory:
Attrib-r-s-h *.*
8. Finding Files With Command Prompt
a. View a list of files / folders in current folder:
DIR *.*
b. View a list of files / folders that are in the current folder, including file / folder is hidden:
DIR *.* / A "A" stands for "ALL"
c. View a list of files (not including the folder) in the current folder:
DIR *.* / AD "D" stands for "DIRECTORY", "-" means exclusion
d. View a list of folders (not including files) in the current folder:
DIR *.* / AD "D" stands for "DIRECTORY"
e. View a list of files / folders hidden:
DIR *.* / AH "H" stands for "HIDDEN"
f. View a list of files / folders sort by name:
DIR *.* / ON for files and folders, "O" means "ORDER BY", "N" means "NAME"DIR *.* / AD / ON to folders onlyDIR *.* / A-D / ON to file onlyDIR *.* / A-DH / ON for any hidden filesDIR *.* / ADH / ON for any hidden folders
g. View a list of files / folders sort by type (extension)
The trick is similar to sorting by name, only "/ ON" replaced with "/ OE".
h. Viewing file list sort by size
The trick is similar to sorting by name, only "/ ON" replaced with "/ OS".For detailed information about the rules of use DIR command, type "DIR /?" And press enter.
9. Suspected Deadly Process
The definition process is a program that runs in the background (background program), does not have a form because it is not made to interact with the user. Unlike the application program that does look at having to interact with the user. Viruses are usually made in such a way that when the virus is running is not visible at all, he is just a process. File viruses are currently running normally can not be deleted because the process is running. Usually the virus files can only be removed once the process is terminated. List of application programs and processes that are running can be viewed using the Windows Task Manager (taskmgr.exe) simply by pressing the Ctrl Alt Del. After the Windows Task Manager window appears, we can choose the "Applications" to see a list of application programs, or "Processes" to see a list of processes. Another option is "Performance", "Networking", and "Users".To stop the running application program, select the name of the application from the list, then click the "End Task". To stop the processes that are running, select the name of the process then click the "End Process". If Windows Task Manager can not be executed, we still can see and stop the processes that are running from the Command Prompt by calling the program "TASKLIST.EXE" to see the process list, then call the program "TASKKILL.EXE" to stop the process.
Example:TasklistTaskkill / F / IM Notepad.exe / IM MSPAINT.EXETaskkill / F / PID 1230 / PID 1253 / T
Description:The parameter "/ F" which was
record-proxy-configuration-server-ubuntu
1. InstallationFirst of all first install squid via synaptic or via the command prompt with:# Apt-get install squidOnce completed then Squid can be configured directly by:# Vi / etc / squid / squid.confBut before the first edit the original file for backup if damaged can be returned to the default:# Cp / etc / squid / squid.conf / etc / squid / squid.conf.bak
2. Configuring SquidFurthermore Squid configuration script:# Vim / etc / squid / squid.confSquid configuration file will appear very long, following the steps that must be considered ....a. HTTP Port: A port used to run Squid# Http_port 3128http_port 192.168.10.1:8080# Log and erroraccess_log / var / log / squid / access.log squiderror_directory / usr / share / squid / errorslogfile_rotate 7
b. Visible Host Name: So that if an error occurs Squid can find a valid hostnamevisible_hostname localhostlocalhost can be replaced with the IP (eg 192.168.10.254) or domain such as proxykoe.comc. Cache Manager: To define the email address of the Squid Cache Managercache_mgr admin@domain.comd. Squid Cache Directory: Defining the location and magnitude squid directory.Figures 500 show directory size in MBFigures 16 shows the number of sub-directory level 1Figures 256 show the number of subdirectories subdirectory level 2 from level 1The number above the higher the bettercache_dir ufs / var / spool / squid 500 16 256e. Filtering: This is an important part of the Squid, by this we can mngatur rule-rule, from anyone who can access the Internet through websites what is allowed to be accessed.
Access List (acl): Anyone who can access the Internetacl all src allacl manager proto cache_objectacl localnet src 192.168.10.1/255.255.255.0################################################## ############ # # BANDWIDTH MANAGEMENT################################################## ############acl admin src "/ etc / squid / adminacl url_regex site "/ etc / squid / site"acl download urlpath_regex "/ etc / squid / download"################################################## ###############acl denied_domains dstdomain "/ etc / squid / denied_domains.acl"
http_access allow manager localhosthttp_access deny manager# Only allow purge requests from localhosthttp_access allow purge localhosthttp_access deny purgehttp_access allow localhosthttp_access allow adminhttp_access deny workhours denied_domainshttp_access allow localnethttp_access deny all# Deny requests to unknown portshttp_access deny! Safe_ports# Deny CONNECT to other ports Than SSLhttp_access allow CONNECT! SSL_ports
# Delay pools 0, for bandwidth managementdelay_pools 3delay_class 1 1delay_class 2 1delay_class 3 1# Unlimitted access to admindelay_parameters 1 -1/-1delay_access 1 allow admindelay_access 1 deny all# Restrictions speed access to "sites" where the maximum speed 2kbps only if # the site more than 64kbdelay_parameters 2 2000/64000delay_access two sites allowdelay_access 2 deny all# Restrictions on access speed to "download", where the maximum speed 1kbps only if # the download more than 32KBdelay_parameters 3 1000/320003 delay_access allow downloaddelay_access 3 deny all
exit the squid.conf and save that have been altered with the command: Wq
how and what we have stated limit access command and the Access List,acl admin src "/ etc / squid / adminthen first we have to do is create and write what in "admin", by:vim / etc / squid / admin
192.168.10.26192.168.10.5192.168.10.4192.168.10.100192.168.10.102192.168.10.157192.168.10.249192.168.10.250192.168.10.15192.168.10.14
Exit and save, with the command,: wqSo on top of IP-IP, is IP that gets full rights as an admin.
acl url_regex site "/ etc / squid / site"- vim / etc / squid / sitesgudanguploadEasySharesavefilemegauploadshareboxingtubemoviefacebook
Exit and save, with the command,: wq
acl download urlpath_regex "/ etc / squid / download", edited with the command:vim / etc / squid / download, and written. / Doc $. / Exe $. / Pdf $. / Xls $. / Docx $. / Mpeg $. / Tar.gz $$ ./tar.bz2$ ./mp3. / Jpg $. / Jpeg $
Exit and save, with the command,: wq
IP Forwarding, for transparent proxy can be implemented, then we have to enable IP Forwarding by giving a value of 1 in the file "/ proc/sys/net/ipv4/ip_forward" by:
# Echo 1> / proc/sys/net/ipv4/ip_forward
But the command must be run auto startup, so if the computer squid die we do not need repot2 run the command continuously.Next we have to run ip_tables for the client to redirect ports our Squid server with the command:
# Iptables-A PREROUTING-t nat-p tcp-dport 80-j REDIRECT-to-port 8800
Then restart the proxy with the command:# / Etc / init.d / squid restart
Make Windows Faster than Before
If your computer is so slow, maybe it's time to empty the contents of the folder "Prefetch" in the Windows folder on drive "system" of the computer. How do go to "System" (usually on drive C), then

go to the Windows folder to the folder in there called Prefetch. Get listed in this folder, you will find as many prefetch files.

Remove all contents of Prefetch folder (remember, you do not delete the prefetch folder delete, just the content only!).

Then exit and restart your computer. After the computer starts, run Disk Cleanup to hard drive system (drive C),

 then restart your computer and its performance will usually be faster than previous
then restart your computer and its performance will usually be faster than previous